Cisco Anyconnect L2tp
Contents
- Please L2TP+IPsec Vs SSL VPN - Cisco Community
- Support L2TP/IPSEC And IPSEC Simultaneously - Cisco
- Cisco Ipsec Windows
- Configuring IPSec Network Security
VPN Bone present you a collection of new protocols, such as OpenVPN, P-Tunnel, Z-Tunnel- S-Tunnel - Kerio - Webproxy - Cisco anyconnect - PPTP - L2TP - SSTP - Https Proxy - Socks -. Secure Pay You can pay invoice via PayPal or BitCoin.
- Allow leasing IP address from Radius server for L2TP, PPTP and CISCO VPN Client Click to lease the IP address to the L2TP, PPTP and CISCO VPN client users through the Radius server. Radius is a protocol that allows network devices to authenticate users against a central database. It can also store technical information used by network devices.
- Your Chromebook has built-in support for VPNs that use L2TP over IPsec. The IPsec layer will either use a pre-shared key (PSK) or user certificates to set up the secure tunnel.
- A VPN is a secured private network connection built on top of publicly accessible infrastructure. The Campus VPN service provides an alternative to using the proxy server for remote access to the UCLA Library and other campus resources. Campus VPN access is restricted to registered students and university employees with an active staff/faculty appointment. You will be required to enroll in.
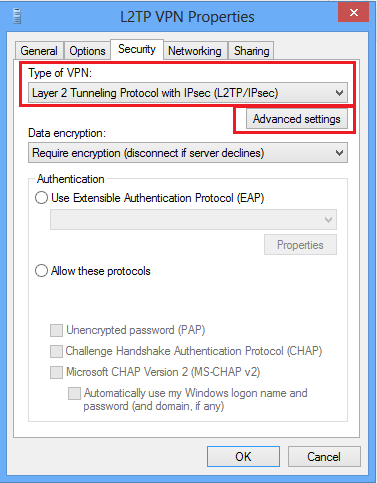
- In “Type of VPN” select “Layer 2 Tunneling Protocol with Ipsec (L2tp/Ipsec). Select “Advanced settings” button, checked “use preshared key for authentication”, Enter 90807060 in the text box then click “Ok”. In data encryption choose “Optional encryption (connect even if no encryption)”.
Introduction
Layer 2 tunneling protocols, such as L2TP, do not provide encryption mechanisms for the traffic it tunnels. Instead, they rely on other security protocols, such as IPSec, to encrypt their data. Use this sample configuration to encrypt L2TP traffic using IPSec for users who dial in.
L2TP tunnel is established between the L2TP Access Concentrator (LAC) and the L2TP Network Server (LNS). An IPSec tunnel is also established between these devices and all L2TP tunnel traffic is encrypted using IPSec.
Prerequisites
Requirements
This document requires a basic understanding of IPSec protocol. To learn more about IPSec, please refer to An Introduction to IP Security (IPSec) Encryption.
Components Used
The information in this document is based on these software and hardware versions.
Cisco IOS® Software Release 12.2(24a)
Cisco 2500 Series Routers
The information presented in this document was created from devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If you are working in a live network, ensure that you understand the potential impact of any command before using it.
Conventions
For more information on document conventions, see the Cisco Technical Tips Conventions.
Configure
In this section, you are presented with the information to configure the features described in this document.
Note: To find additional information on the commands used in this document, use the Command Lookup Tool (registered customers only) .
Network Diagram
This document uses the network setup shown in this diagram. The dial up user initiates a PPP session with the LAC over the analog telephone system. After the user is authenticated, the LAC initiates an L2TP tunnel to the LNS. The tunnel end points, LAC and LNS, authenticate each other before the tunnel is created. Once the tunnel is established, an L2TP session is created for the dialup user. To encrypt all the L2TP traffic between the LAC and LNS, the L2TP traffic is defined as the interesting traffic (traffic to be encrypted) for IPSec.
Configurations
This document uses these configurations.
| LAC Configuration |
|---|
| LNS Configuration |
|---|
Verify
This section provides information you can use to confirm your configuration is working properly.
Certain show commands are supported by the Output Interpreter Tool (registered customers only) , which allows you to view an analysis of show command output.
Peak hour traffic. Itunes download macbook pro 2020. Use these show commands to verify the configuration.
show crypto isakmp sa— Displays all current IKE security associations (SAs) at a peer.
show crypto ipsec sa—Displays the settings used by current SAs.
show vpdn—Displays the information about the active L2TP tunnel.
Troubleshoot
This section provides information you can use to troubleshoot your configuration.
Please L2TP+IPsec Vs SSL VPN - Cisco Community

Support L2TP/IPSEC And IPSEC Simultaneously - Cisco
Troubleshooting Commands
Certain show commands are supported by the Output Interpreter Tool (registered customers only) , which allows you to view an analysis of show command output.
Note: Before issuing debug commands, please see Important Information on Debug Commands.
Cisco Ipsec Windows
debug crypto engine—Displays engine events.
Install docker in rhel 8. debug crypto ipsec—Displays IPSec events.
debug crypto isakmp—Displays messages about IKE events.
debug ppp authentication—Displays authentication protocol messages, including CHAP packet exchanges and Password Authentication Protocol (PAP) exchanges.
debug vpdn event—Displays messages about events that are part of normal tunnel establishment or shutdown.
debug vpdn error—Displays errors that prevent a tunnel from being established or errors that cause an established tunnel to be closed.
debug ppp negotiation—Displays PPP packets transmitted during PPP startup, where PPP options are negotiated.
Configuring IPSec Network Security
Related Information
